This is a writeup of one of the more challenging exercises in Juice Shop: forging a coupon code with a discount of more than 80%.
Category: cryptographic issues
Vulnerability: create coupons that give a discount of 80% or more.
Below I will show the steps for completing this challenge.
Find the list of dependencies in /ftp
The first step is to visit the FTP folder on the app by going to /ftp. Here you will see a few different files. When you try to open one of the .bak, .yml or .pyc files you get an error that only .md and .pdf files are allowed.
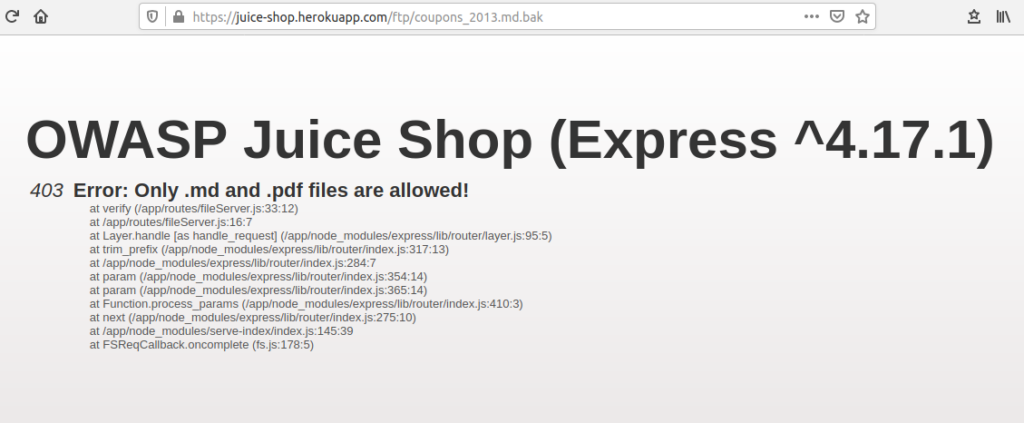
By adding %2500.md to the url you can actually access the files. This is a way to trick the application to think that you are opening a .md file. This works because of the null byte %00 which is url encoded as %2500.
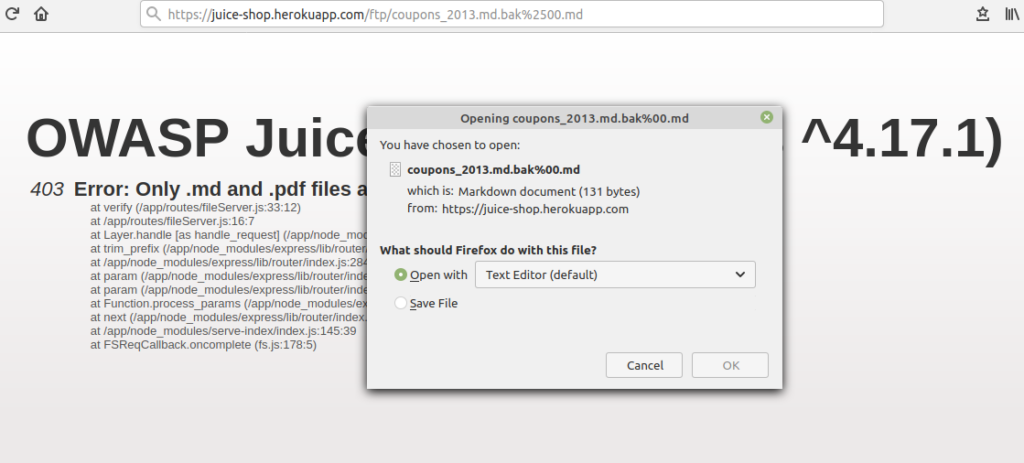
Open the file package.json.bak by changing the URL from /ftp/package.json.bak to /ftp/package.json.bak%2500.md
Dependencies
In this file you can find a list with dependencies (software ‘packets’ that Juice Shop makes use of).
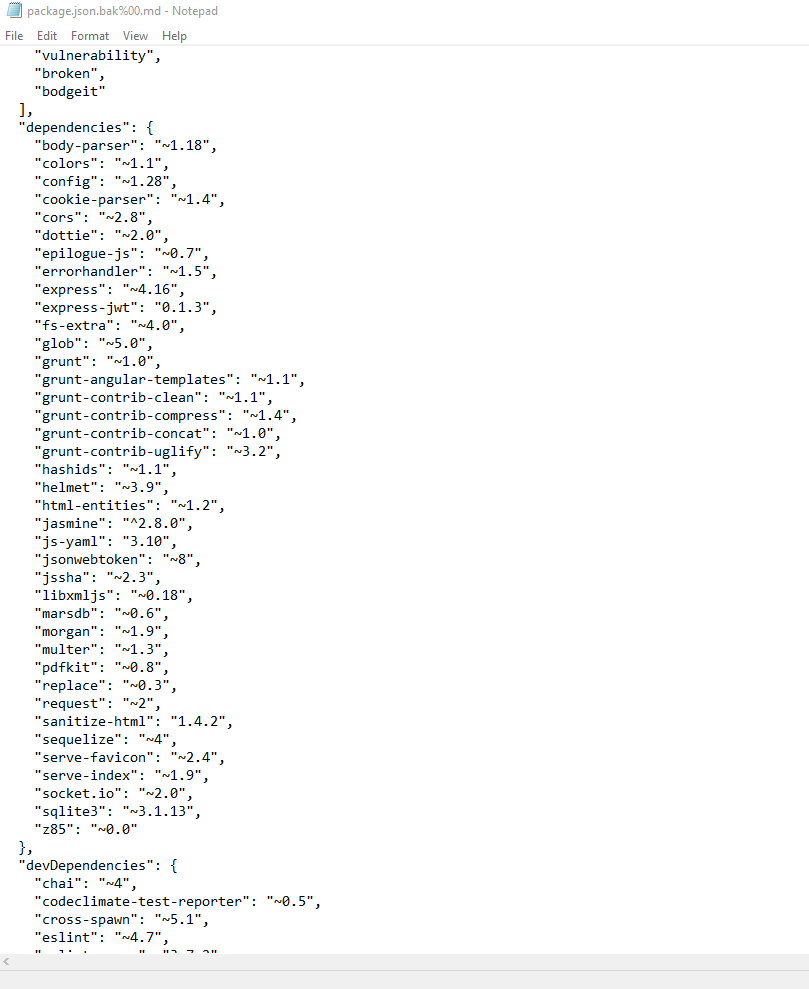
When you look for these dependencies on Google you find a few that could be related to generating codes. Those are ‘hashids’ and ‘z85’.
Decoding Juice Shop coupons
Juice Shop has a Twitter account. Every month it posts coupons that give you a certain discount.
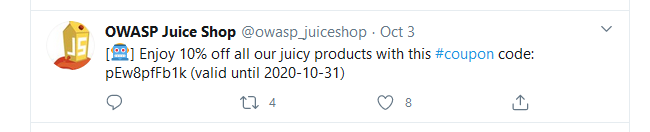
You can find out if Juice Shop uses one of the programs we found (hashids or z85) by using those programs to decode those coupon codes and looking at the result. If the result seems to have a kind of structure to it, we may use that structure to create coupons ourselves.
If you look up Hashids you will find that you can only generate codes with it using a number. Also the name Hashids suggests that the code will be hashed. Hashes only go one way, they can’t be decoded.
But z85 can be decoded. When you try this on the Juice Shop coupons you will find out this is the program that was used to create the coupons. We will look at this in the next step.
Installing z85
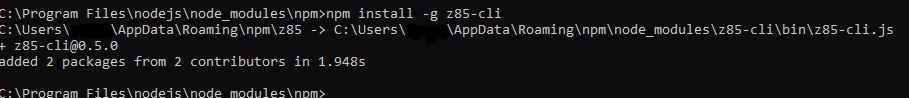
In order to use z85 you first need to install NodeJS from nodejs.org. Then you can install z85 as follows:
- open a command prompt as administrator and navigate to nodejs/node_modules/npm
- execute the following command: npm install –g z85-cli
With z85 -d [code] you can decode a coupon.
When we decode the coupon from October shown in the Twitter post above, we get OCT20-10.
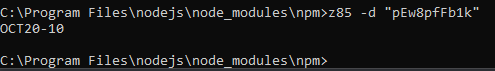
This is a pattern! OCT is for October, 20 is for 2020 and 10 is for 10% discount.
Generating a coupon code with z85
To generate a coupon with a discount of 80% we can see what we get when we encode OCT20-80. You can try to generate a coupon for the current year and month.
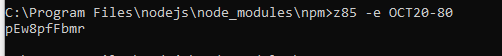
Result: pEw8pfFbmr
Trying the Coupon
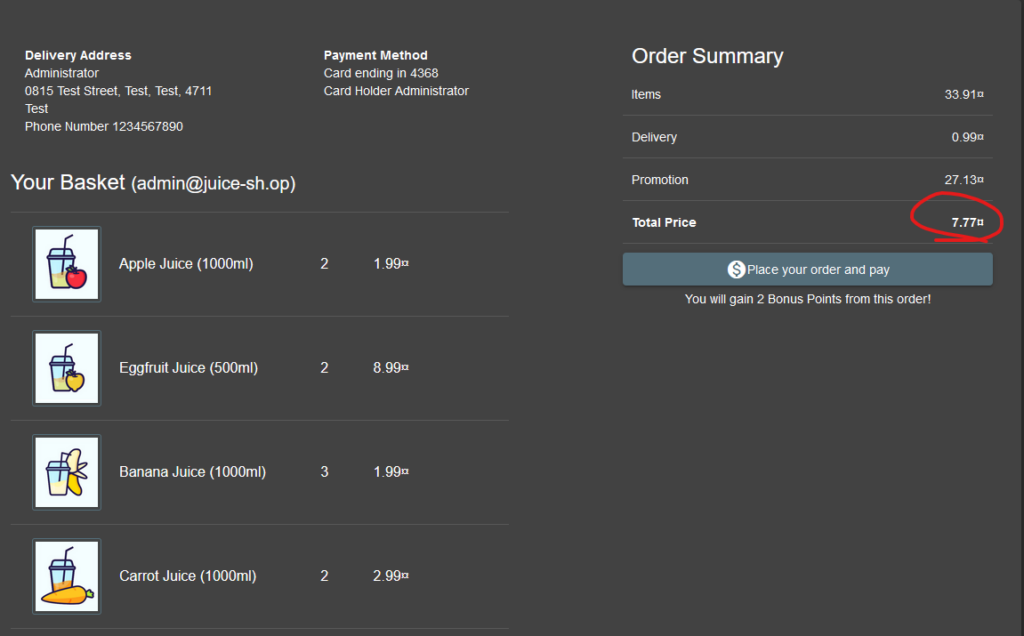
Placing an order.
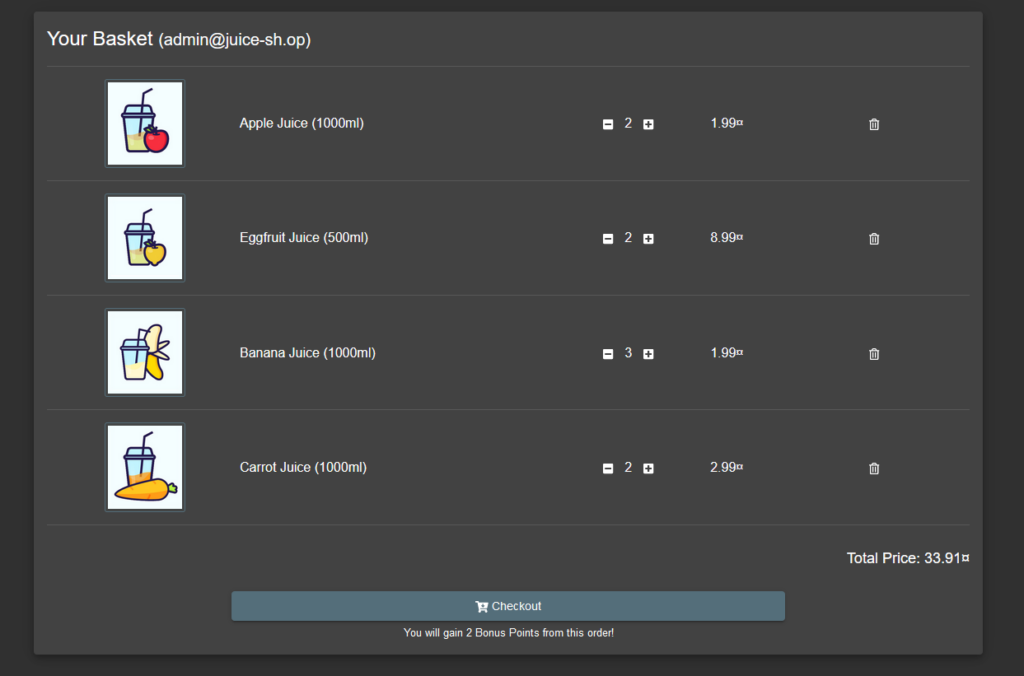
Enter the generated coupon: pEw8pfFbmr.
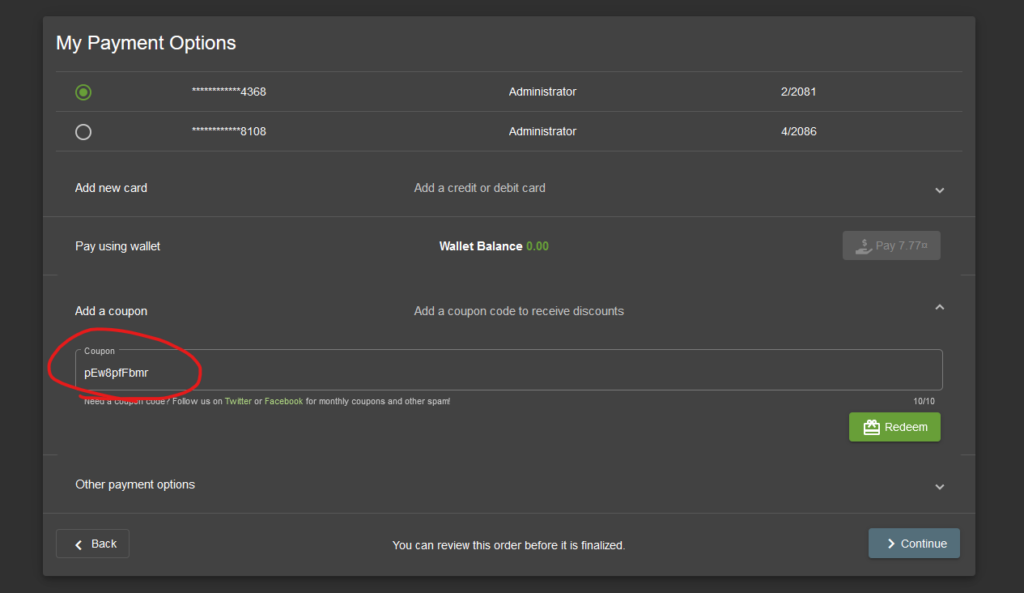
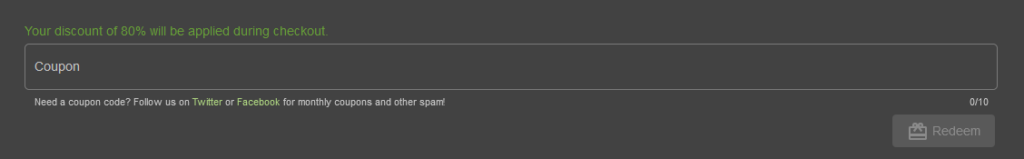
Continue.
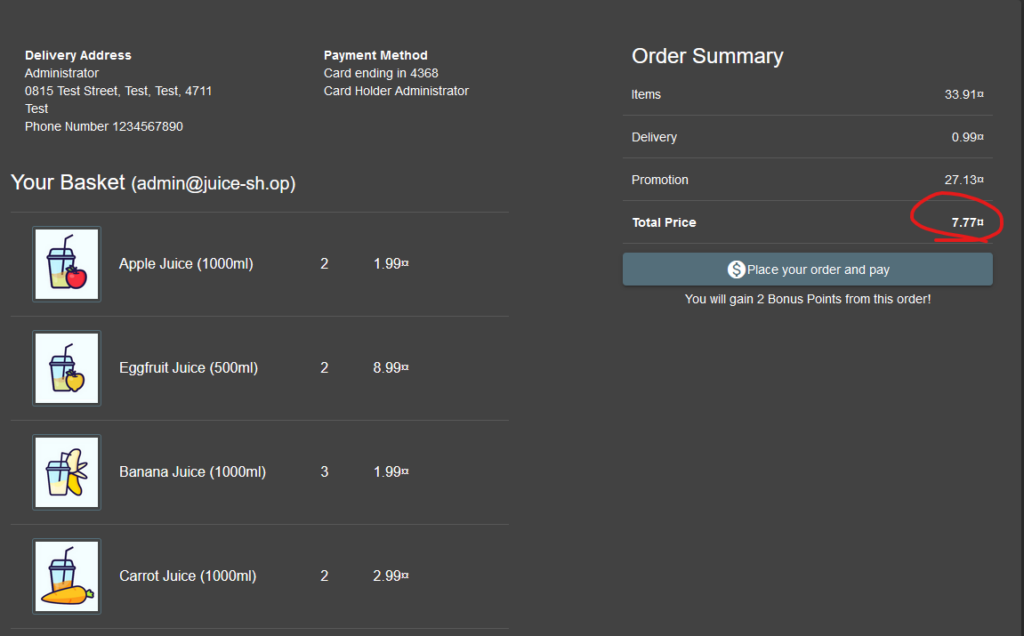
As you can see the total price went from 33 to 7.77. The coupon works!
Possible solutions
- You could perhaps limit the damage that can be done by rejecting coupons with a discount above 50%. But this is not a complete solution.
- Make sure that it’s not possible to find out which algorithm is used to generate the codes. Maybe it’s possible to deny access to the /ftp section by adding an access rule to the .htaccess file of the website.
- An option would be to generate coupons in such a way that’s hard to replicate or reverse engineer. For example you could hash the coupons instead of encoding them or use a unique algorithm that is not publicly available.
- Using phrases that are less predictable than OCT20-10 for generating the coupons.
Sources
- https://medium.com/@briskinfosec/null-byte-sql-injection-4cc34ae4e7d7
- https://twitter.com/owasp_juiceshop?lang=nl
- https://github.com/niieani/hashids.js
- https://hashids.org/
- https://www.npmjs.com/package/z85-cli
- https://github.com/bkimminich/z85-cli
- https://stackoverflow.com/questions/11728976/how-to-deny-access-to-a-file-in-htaccess
- https://serverfault.com/questions/952712/htaccess-rule-to-protect-against-malicious-post-requests-to-wordpress-index-php
- https://bkimminich.gitbooks.io/pwning-owasp-juice-shop/content/appendix/solutions.html