This is a summary of the Red Team OPSEC room in TryHackMe.
To be honest this room was a bit confusing to me because it talked about risks and vulnerabilities in Red Teaming. Normally you use these terms to talk about companies and software. What are the risks for the company, what is this software vulnerable to, etc.
Below I’ll try to summarize each section of the TryHackMe room.
Introduction
The introduction to this room explains OPSEC and the five steps of OPSEC. OPSEC is explained from the perspective of the Red Team. The goal in this case is not to protect information (the task of the Blue Team) but to protect the processes within the Red Team. The goal is that it’s very hard for the Blue Team to know what the Red Team is doing.
The five steps of OPSEC are:
- Identifying critical information
- Analyze threats
- Analyze vulnerabilities
- Assess risks
- Take the right measures
This TryHackMe room has a section for each of the steps in OPSEC. Let’s take a look at them.
Critical Information Identification
Critical information in this context is information that could expose the plans of the Red Team to the Blue Team, enabling them to take preventive measures.
Examples of critical information:
- Customer data which the Red Team has collected.
- Red Team information like identities, activities, plans and limits.
- Tactics, Techniques and Procedures.
- Operating system, hosting provider.
- IP addresses.
- Registered domain names.
- Hosted websites.
The assignment in this section was to select critical information from several options. Let’s see the correct answers.
Your team uses:
- A Lynx text-based web browser.
- Offensive Linux distributions hosted on cloud provider X.
- A domain with the name ‘webmai1.thm’ to host a phishing site.
All this falls under critical information because it gives insight into the plans of the Red Team.
Threat Analysis
The next step is to analyze threats to the operations of the Red Team. For that we need to answer the following questions:
- Who is the adversary?
- What are the goals of the adversary?
- Which TTP’s (Tactics, Techniques, Procedures) does the adversary use?
- Which critical information did the adversary collect?
Here it’s clear who the adversary is and what his goal is. The adversary is the Blue Team and its goal is to protect the network and system of an organization. Another possible adversary is a real hacker / group of hackers. Each adversary with the intention and capacity to undermine the work of the Red Team forms a threat.
Vulnerability Analysis
A vulnerability in OPSEC is something different than a typical vulnerability in cyber security. In OPSEC a vulnerability means that an adversary is able to do things to counter your plans.
An example of an OPSEC vulnerability is using the same IP address for different attacks. This makes it easier for the Blue Team to identify the attacker and if they block this IP address, the other parts of the attack will fail too.
Another example is a Red Team that stores collected information in a badly protected database. If hackers get into the database and extract the information from it you have indirectly leaked information of the client (the organisation of the Blue Team). Lastly it wouldn’t be a good idea to put information about the assignment / pentest on social media.
Assignment
In this assignment a few different situations are mentioned and you need to indicate whether they are OPSEC vulnerabilities or not.
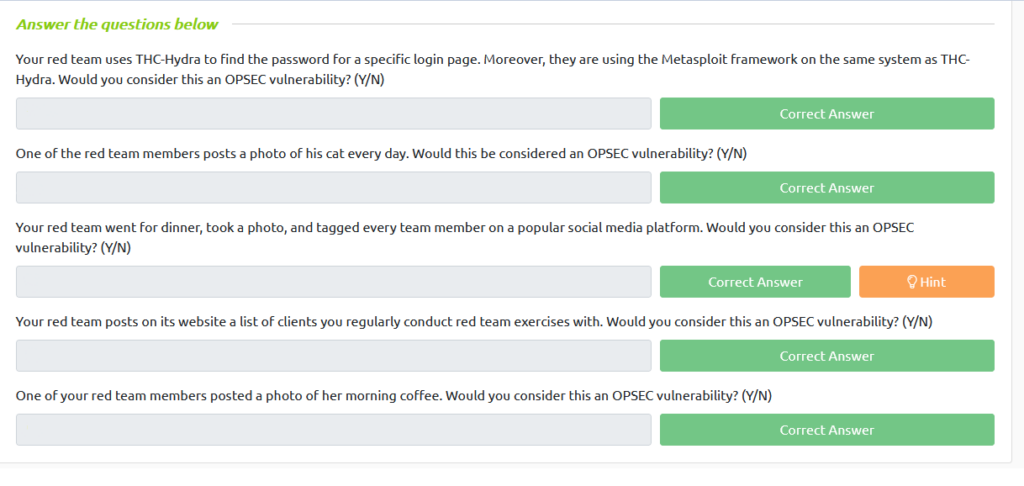
Let’s go through each question and see if they are a vulnerability or not:
- Question: The Red Team uses THC-Hydra and Metasploit on the same system.
- Answer: Yes. It would be better to use these tools on different systems if possible. If one attack is blocked, the other one may still succeed.
- Question: One of the Red Team members posts a picture of his cat every day.
- Answer: No. Pictures of a cat don’t give a lot of information about the pentest itself.
- Question: The Red Team has posted a picture of all teammembers and tagged their names.
- Answer: Yes. This gives information about the members of the Red Team. You could now look them up and estimate how they may work, what their process may be like.
- Question: The Red Team posts a list of regular clients on their website.
- Answer: Yes. This discloses important information about the Red Team.
- Question: A Red Team member posts a picture of his morning coffee.
- Answer: No. This may be personal, but there isn’t a lot of useful information we can get from it.
Risk Assessment
The goal of risk assessment in OPSEC is to estimate the risk that an adversary will exploit one of the weaknesses / vulnerabilities in the Red Team. For that we need to estimate the capabilities of the Blue Team.
An example of something that could interfere with the activities of the Red Team is if the Blue Team uses a SIEM. Therefore this counts as a high risk.
Because of the SIEM, the Blue Team is better able to detect attacks.
On the other hand if we were to know that the Blue Team has little capabilities to detect an attack, the risk is low.
The example of the database in the previous sections also creates a risk. The internet is constantly scanned for badly secured websites and databases, so the risk that this insecurely stored information leaks is quite high.
Countermeasures
The goal of countermeasures is to prevent that the adversary gets to know important information or to present the information in such a way that it can be misinterpreted (deception).
An example of a countermeasure is to use a different IP address for each attack so that different parts of the attack can continue when one of them is blocked. A countermeasure to protect the database is to isolate it from the internet.
More Practical Examples
In this section the practical measures you can take for Red Team OPSEC are repeated. One example of such a measure is to change the hostnames you use to attack. For example if your host is called ‘Attackbox’ you can change it to a less suspicious name.
Then there is a final assignment where you need to indicate which statement belongs to which step in OPSEC. To be honest I thought this assignment was a bit confusing.
So that was it, this was the Red Team OPSEC room in TryHackMe.