Juice Shop is a platform that contains a lot of vulnerabilities. It was made for people to practice their ethical hacking skills. The vulnerability we’re going to discuss here is using SQL injection to log in as admin.
Category: injection
Vulnerability: It’s possible to login on the admin account via an SQL injection
How to do it
Go to the login page in Juice Shop and type in the following credentials:
- Email: ‘ or 1 = 1 – –
- Password: –
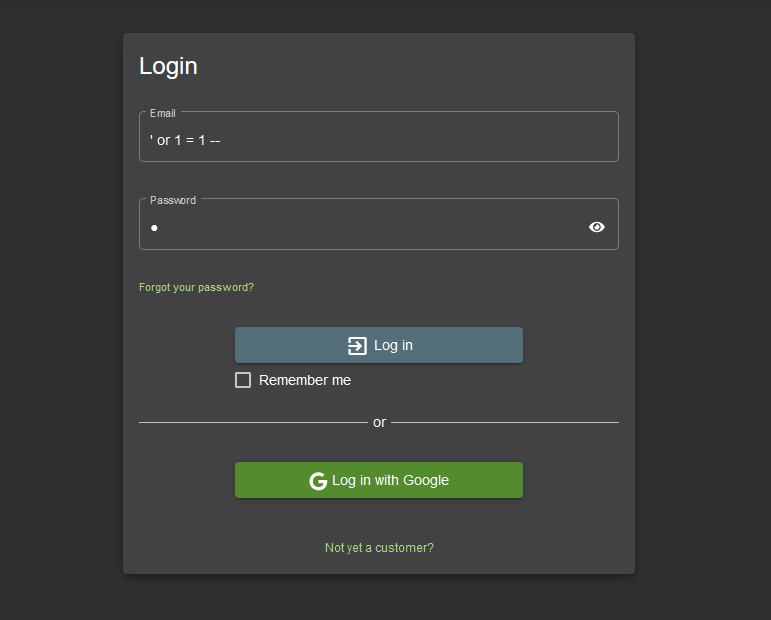
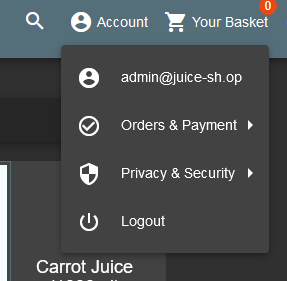
We are now logged in on the Admin account. The injection happens in the e-mail field in this case. It doesn’t matter what you type in the password field.
The same can be done with:
- Email: ‘ or “”=”” – –
- Password: –
Or with:
- Email: admin@juice-sh.op’- –
- Password: –
Short explanation of SQL injection
SQL is a programming language that is used to communicate with a database. With commands like SELECT * FROM Users you can get information from a table called ‘Users’.
Normally it’s impossible as a user to execute SQL commands on a website. But with an SQL injection this is exactly what an attacker tries to do.
Explanation of: ‘ or 1=1 – –
I will divide this command in a few sections and explain what they do.
The quotation mark ‘ at the start of the command: In this case the website expects a username. A quotation mark is then added to close the query to the database. But when you type a ‘ at the end of the username, you are ending the query already. So everything you type after this is seen as SQL and will be executed.
or 1=1
In SQL, or 1=1 is a statement that is always true. The same is true for “”=””. This is the part of the code that bypasses having to know the password. With the statement we have now, ‘ or 1=1, we have actually made sure that it’s true no matter what. Normally the statement is true only if the password is correct. But now the statement is true even without needing a password, because adding or 1=1 makes it always true.
– –
In SQL you can use – – to comment out the code that comes after. So because of these two minus signs at the end of the SQL injection, the code that comes after this is ignored and not executed.
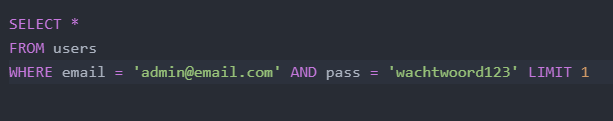
Example in the code: This is what the code may look like when you type in normal credentials: Email: admin@email.com Password: wachtwoord123
When you type in ‘ or 1=1 – -, you will get:
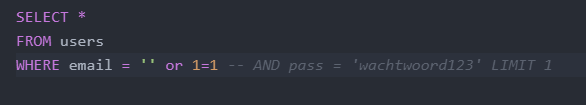
The code from Juice Shop probably looks different, but this is approximately what happens with an SQL injection.
There are different types of prevention for SQL injection. We will briefly discuss one of them.
Possible solution: escaping user input
One of the ways to solve this vulnerability is by escaping user input. Everything that is different from the information that you would expect in a login form is not accepted. So when a user types ‘ this is seen as invalid input. This can make potential SQL injections harmless.
Sources:
- https://www.w3schools.com/sql/sql_injection.asp
- https://www.hacksplaining.com/prevention/sql-injection
- https://www.hacksplaining.com/exercises/sql-injection#/start
- https://bkimminich.gitbooks.io/pwning-owasp-juice-shop/content/appendix/solutions.html

Howdy I am so thrilled I found your web site, I really found you by error, while I was searching on Google for something else, Regardless I am here now and would just like to say thanks for a marvelous post and a all round enjoyable blog (I also love the theme/design), I don’t have time to read it all at the moment but I have book-marked it and also added in your RSS feeds, so when I have time I will be back to read a great deal more, Please do keep up the awesome job.
Thanks for your nice comment!
Have you ever considered about including a little bit more than just your articles? I mean, what you say is valuable and all. However think of if you added some great graphics or video clips to give your posts more, “pop”! Your content is excellent but with pics and video clips, this blog could definitely be one of the best in its field. Superb blog!
Thanks man! I will consider it 🙂